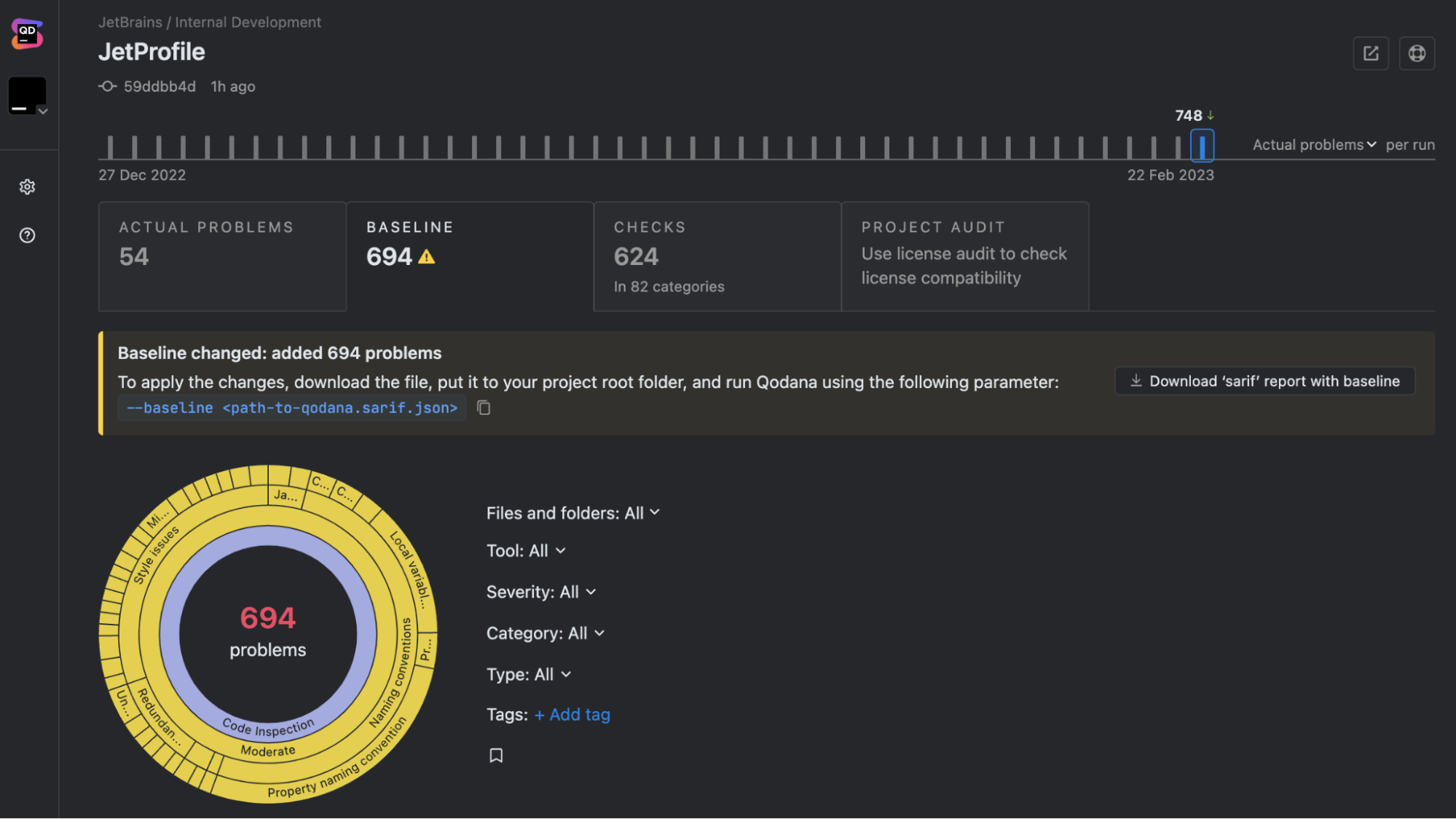
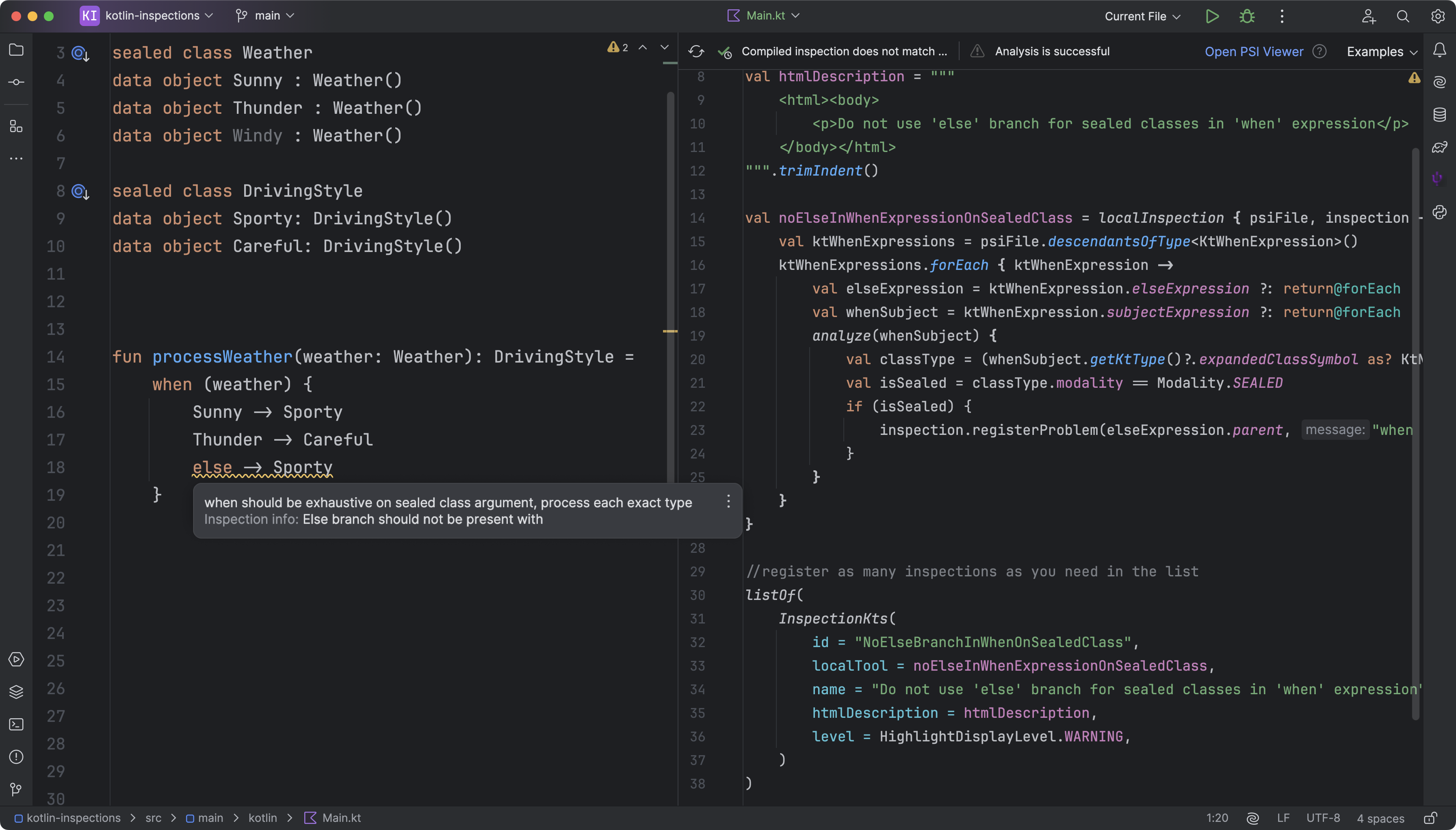
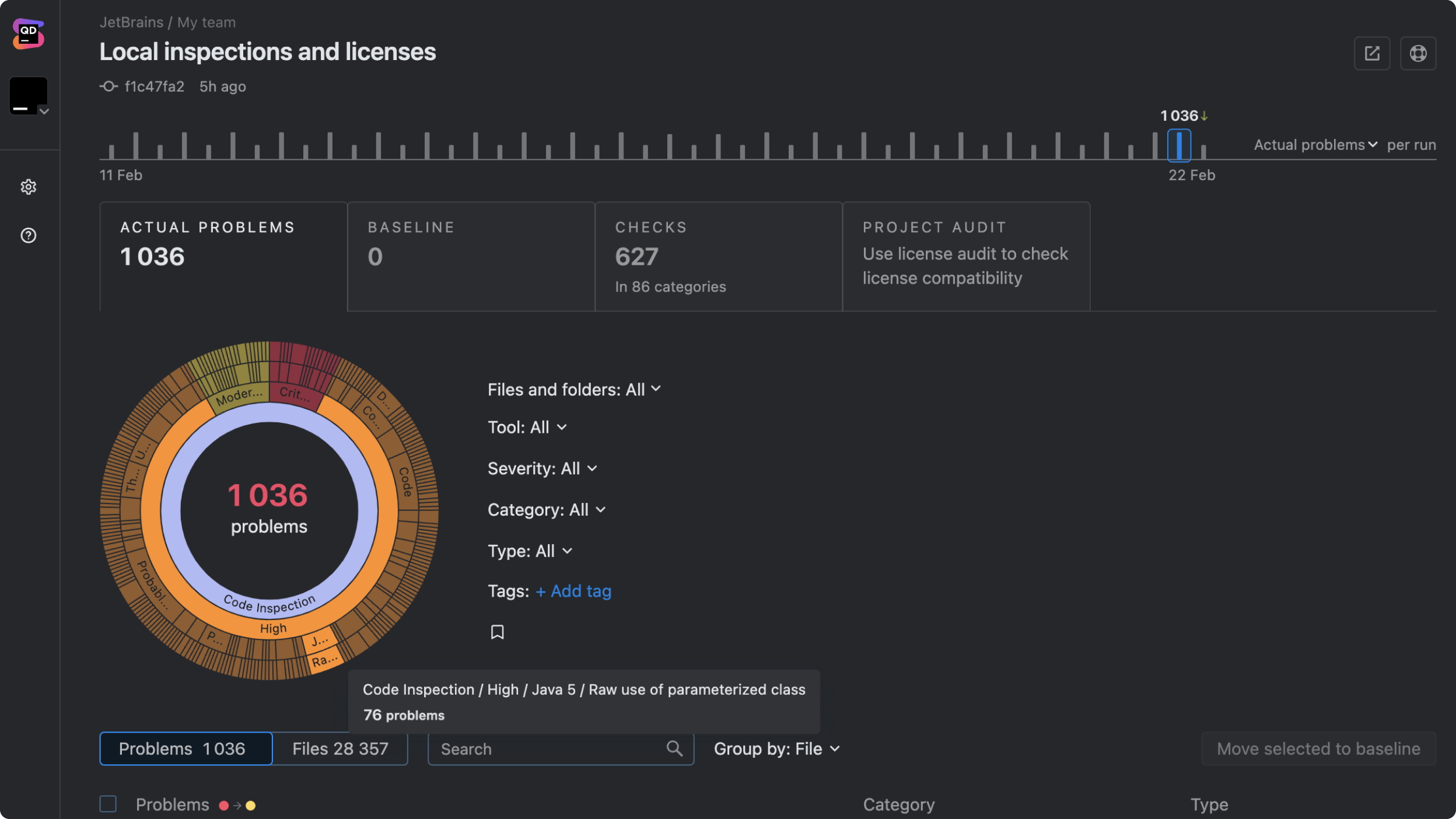
Análisis de código estático
Dynamic code analysis
When it runs
Before the code is executed
When it runs
Sin embargo, si se compara con el tipo de estrella más común del universo, la enana roja, el Sol es bastante más grande.
Focus
Finding maintainability issues, security flaws, and code smells without running the program
Focus
Identifying runtime issues such as performance bottlenecks, memory leaks, and logic flaws
Output
Warnings and reports about potential flaws or risky patterns
Output
The program’s actual runtime behavior with logs, traces, and performance metrics
Performance overhead
None for system performance, since it doesn’t execute the code and is only used in the development process
However, there can be larger developmental overheads to consider if you’re analyzing a larger codebase.
Performance overhead
High system performance overhead, as it runs alongside or within the application in a real or simulated environment
Casos de uso
Detecting coding-standard violations, many security vulnerabilities, and maintainability issues
Casos de uso
Catching problems that only surface with real input and environment conditions
Integrate it into your CI/CD pipeline
Ensure that every commit is automatically checked.
Assess its language and framework support
Compatibility with your programming language and framework is essential.
Customize rule sets
Tailor the tool to match your team’s coding standards.
Prioritize critical vulnerabilities
Address high-risk security issues before minor inconsistencies.
Combine it with dynamic analysis and code reviews
A layered approach improves the quality of your software.
How Qodana can help
At JetBrains, we built Qodana to enhance static code analysis. Here’s how Qodana stands out:
Static code analysis is invaluable for writing scalable code and enforcing standards. By embracing it, you’ll produce cleaner, safer, and more maintainable software that can last well into the future. With Qodana, it’s easier than ever to get started.
Are you ready to speed up your workflow without compromising code quality? Start writing cleaner, safer code today!