OpenID Connect
OpenID Connect 1.0, as defined by the OpenID Specification, is an identity layer built on OAuth 2.0. It allows client applications to validate an end-user's identity through authentication performed by an authorization server. IT also facilitates the retrieval of user profile details in an interoperable, REST-like fashion.
Using Hub as an OpenID Provider (OP) means configuring the service to authenticate users and issue OpenID Connect tokens. As an OP, Hub acts as a trusted identity provider, allowing users to use their existing credentials to authenticate with other applications or services that support OpenID Connect.
Hub OpenID Connect Endpoint
Hub supports auto-discovery for the OpenID Connect. Thus, OpenID Connect Endpoint for your Hub service is as follows:
If your client service does not support auto-discovery, then use the following endpoints for your Hub as the OpenID Connect provider:
End-point type | End-point URL |
|---|---|
Authorization endpoint |
|
Token endpoint |
|
User info endpoint |
|
JWKS endpoint |
|
General Configuration
In order to use Hub as an OpenID Provider, you need to add a service that redirects authenticated users back to the service that originates the authentication request. You then can then use the client ID, client secret, and endpoint for your Hub service to register the connection in the external client application.
To use Hub as an OpenID Connect Provider
From the Server Settings section of the Administration menu, select Services.
Click the New service button.
Enter a Name for the service and its Home URL, then click the Create button.
Hub opens the Settings tab for the new service.
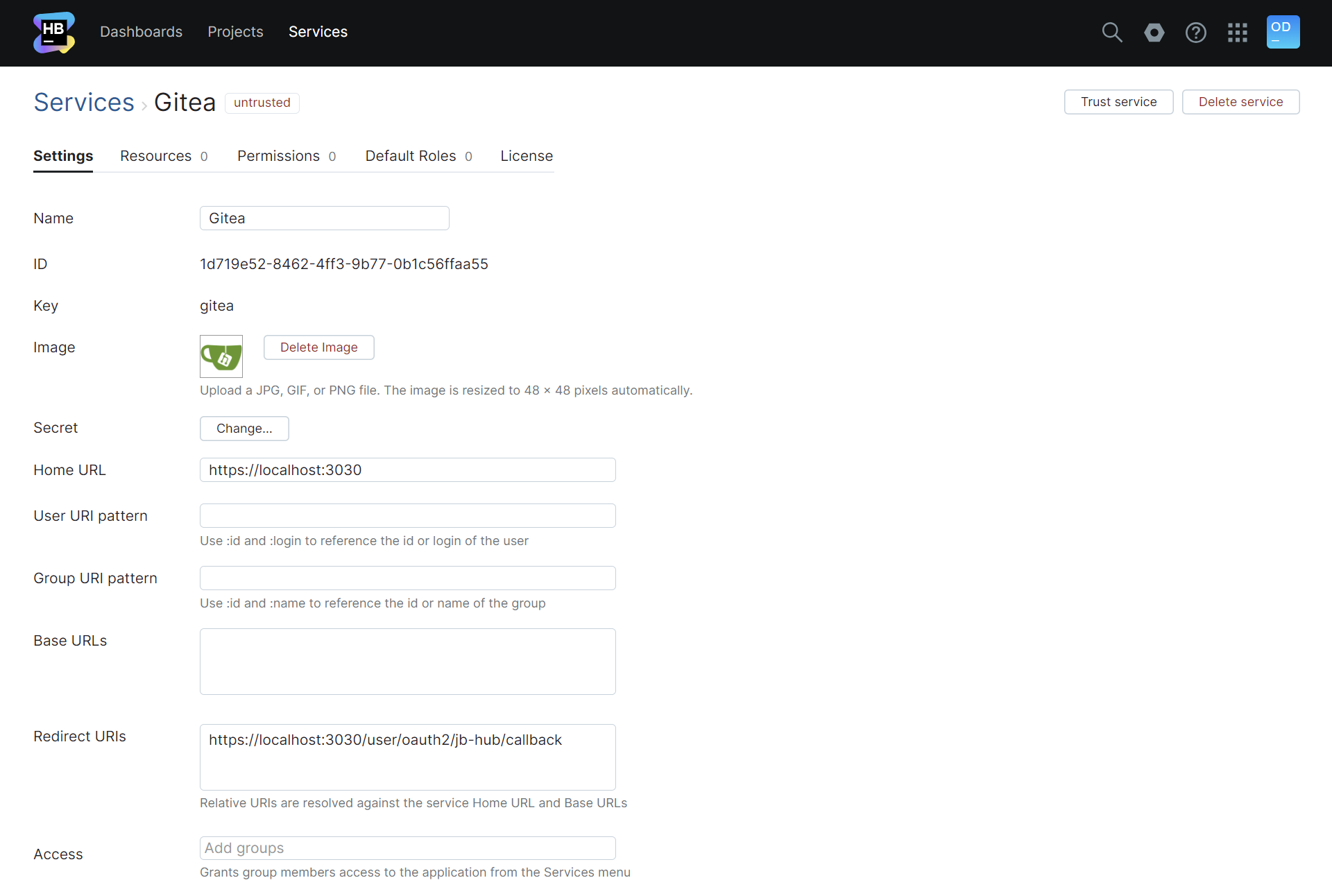
For the the Redirect URIs, enter the web address where Hub should redirect authenticated users.
In your external client application, provide the client ID, client secret, and endpoint of the Hub service.
For the client ID, use the value that is shown as the ID on the Services page in Hub.
For the client secret, click the Change button next to the Secret field in the service settings. Copy the value shown as the New Secret for use in the external client application, then click the Change Secret button.
For the auto discovery endpoint URL, use the following format:
<Hub Service BaseURL>/.well-known/openid-configuration