TLS Server Certificates and Keystores
To secure the connection to your Hub server with the built-in TLS, you must have a server certificate and private key, or a keystore.
For a production environment, we urge you to obtain an SSL certificate from a trusted Certificate Authority.
However, for testing and evaluation purposes, you can use a self-signed certificates. There are several tools that let you create SSL keys and certificates. This page describes a procedure for creating a self-signed server certificate with the OpenSSL toolkit.
Create a Self-signed Server Certificate
Create a self-signed server certificate with the OpenSSL
Generate a new 2048 bit RSA key:
openssl genrsa -out Hub_Server_TLS.pem 2048Generate a certificate request for the generated key:
openssl req -new -key Hub_Server_TLS.pem -out Hub_Server_TLS_req.csrAs the Common Name parameter, set the fully qualified domain name (FQDN) of your server. The service will be available through the generated server certificate by the URL:
https://<FQDN of your server>:<port>/To generate a certificate of the v3 version, you need to preliminary create a configuration file and provide it during the certificate generation. Create a text configuration file, let's name it
v3.ext, with the following content:authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEnciphermentGenerate a v3 certificate:
openssl x509 -in Hub_Server_TLS_req.csr -out Hub_Server_TLS_cert.pem -req -signkey Hub_Server_TLS.pem -days 3650 -extfile v3.extResult: You have a self-signed server certificate
Hub_Server_TLS_cert.pemand its private key that are ready for upload to Hub. To secure your installation, upload the private key and certificate during a standard installation or upgrade.
To install the certificate and private key:
Start a standard installation or upgrade procedure that is appropriate for your current installation and operating system. For specific instructions, see Installation and Upgrade.
Once the web-based configuration wizard launches, select the option to Set up or Upgrade your installation.

On the Confirm Settings page, switch to the HTTPS configuration. In the Server Certificate section, switch to the Private key and certificate settings.
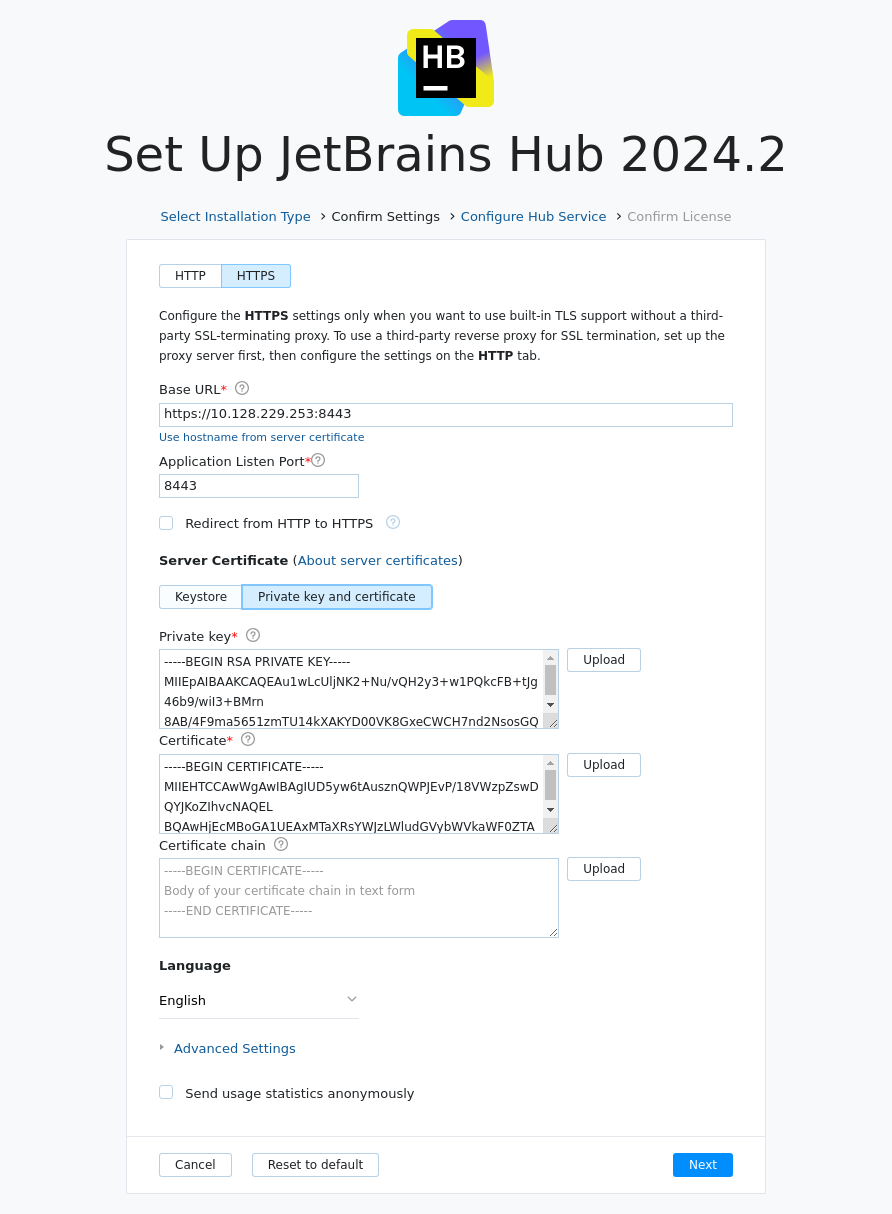
For the Private key, upload the newly created
Hub_Server_TLS.pemfile.For the Certificate, upload the newly created
Hub_Server_TLS_cert.pemfile.Continue with the standard installation or upgrade. When done, traffic to your Hub server is secured using the self-signed certificate.