Find vulnerable and malicious dependencies
Large and complex projects usually have a number of third-party dependencies that enhance productivity by extending the functionality of common libraries and frameworks.
However, relying on third-party code raises security concerns, as it may involve the use of vulnerable dependencies in your project.
The bundled IntelliJ IDEA Package Checker plugin is powered by https://www.mend.io/jetbrains-lp/?utm_source=JetBrains. The plugin analyzes Gradle, Maven, NPM, PyPI, NuGet, and sbt dependencies for known vulnerabilities. It allows you to handle such cases by retrieving information about a vulnerable dependency and updating it to the latest released version.
Enable the Package Checker plugin
This functionality relies on the Package Checker plugin, which is bundled and enabled in IntelliJ IDEA by default. If the relevant features are not available, make sure that you did not disable the plugin.
Press Ctrl+Alt+S to open settings and then select .
Open the Installed tab, find the Package Checker plugin, and select the checkbox next to the plugin name.
Vulnerable dependencies
Fix vulnerable dependencies in the editor
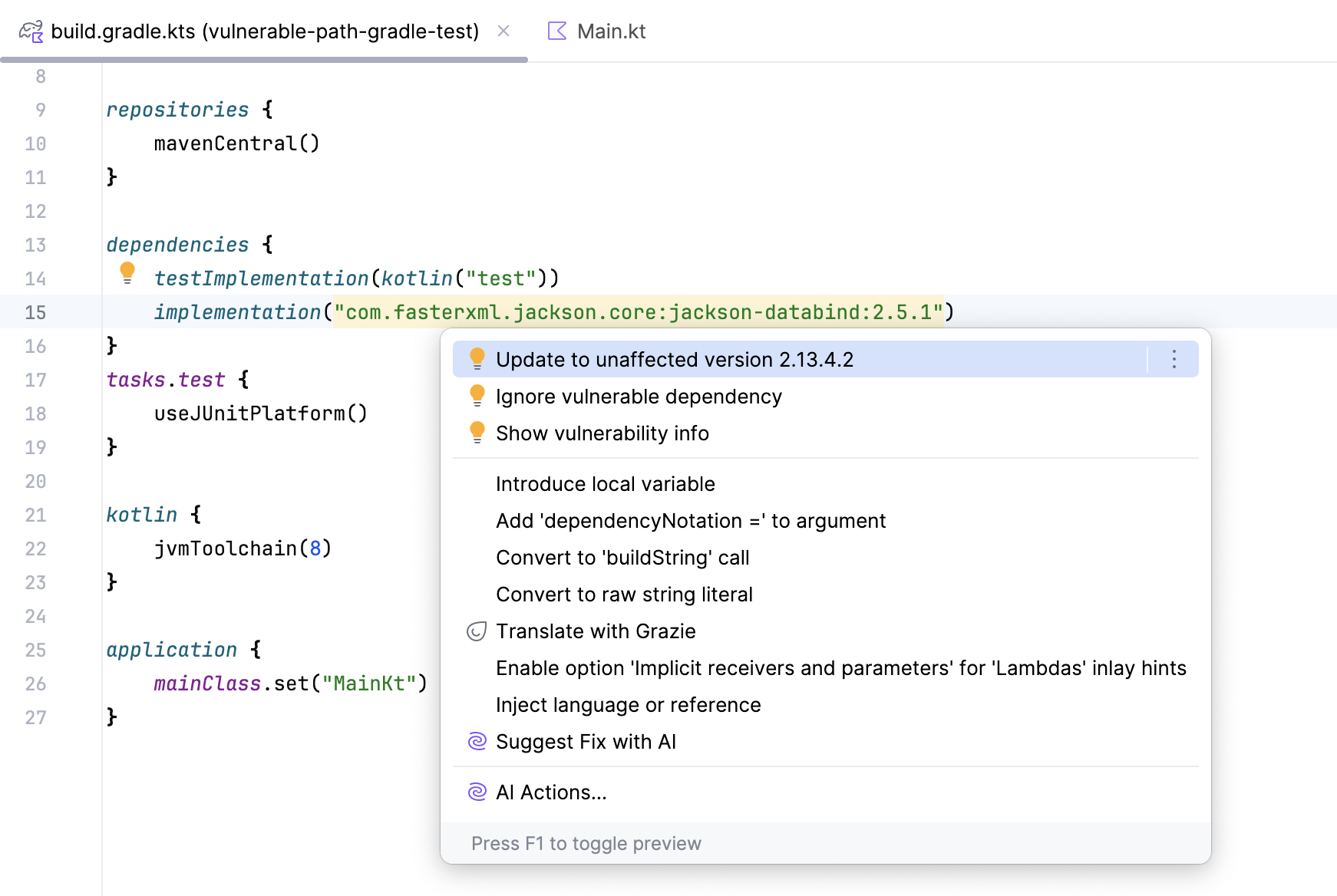
Open pom.xml or build.gradle in the editor.
The IDE highlights packages that are considered vulnerable.
Place the caret at a highlighted package and press Alt+Enter to see the suggested fixes. They may suggest updating to a safe version, visiting the Mend.io website to learn more about a particular vulnerability, or ignoring the vulnerability.
Analyze code to find all vulnerable dependencies
In addition, you can run an inspection to display the list of all declared and imported vulnerable dependencies in the project.
In the main menu, navigate to .
Alternatively, right-click a folder or a file in the Project tool window Alt+1 (for example, pom.xml or build.gradle) and select .
The result is displayed on the Vulnerable Dependencies tab of the Problems tool window ( or Alt+6) .
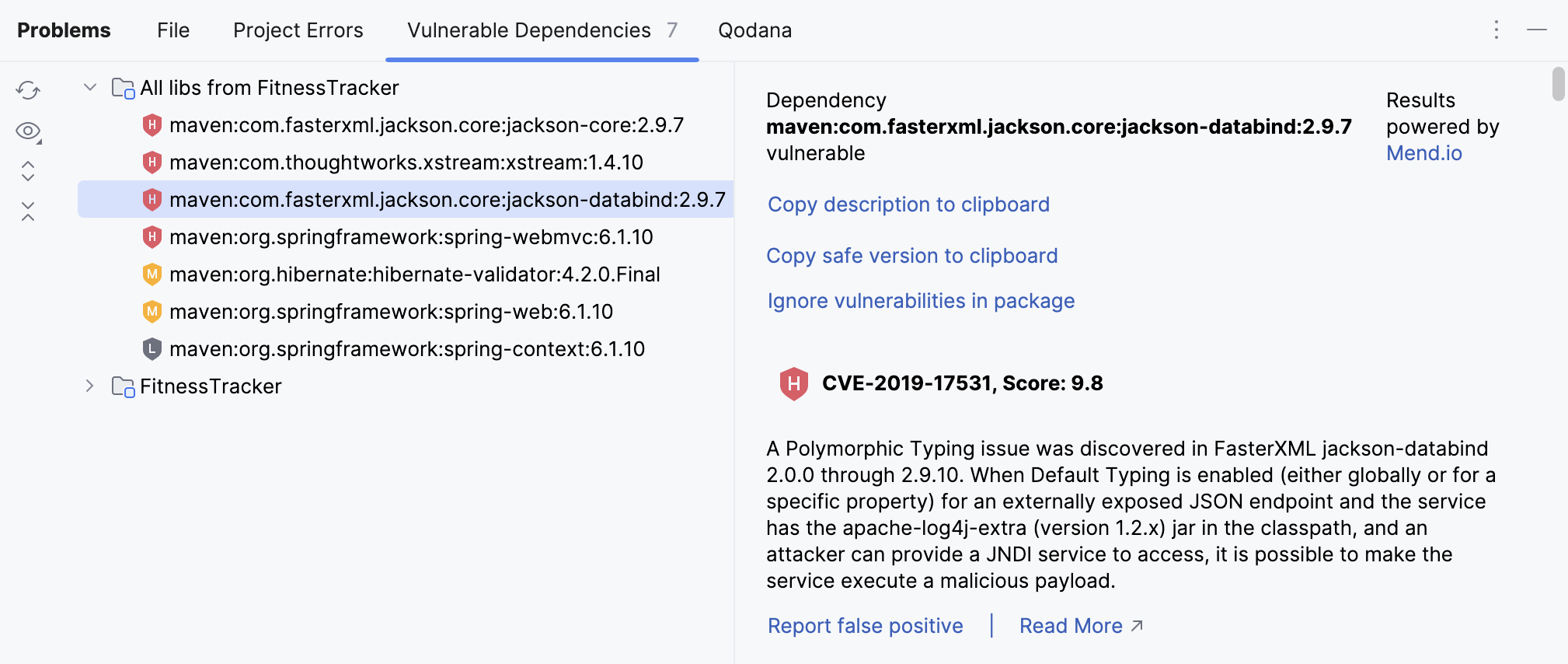
For each vulnerability, you can see an indication of the severity. Click a specific dependency to see more information about the vulnerabilities that were found in that dependency.
Ignore vulnerabilities
Ignored vulnerabilities are added to a list in inspection settings. If required, you can share the profile with this list with other members of your team.
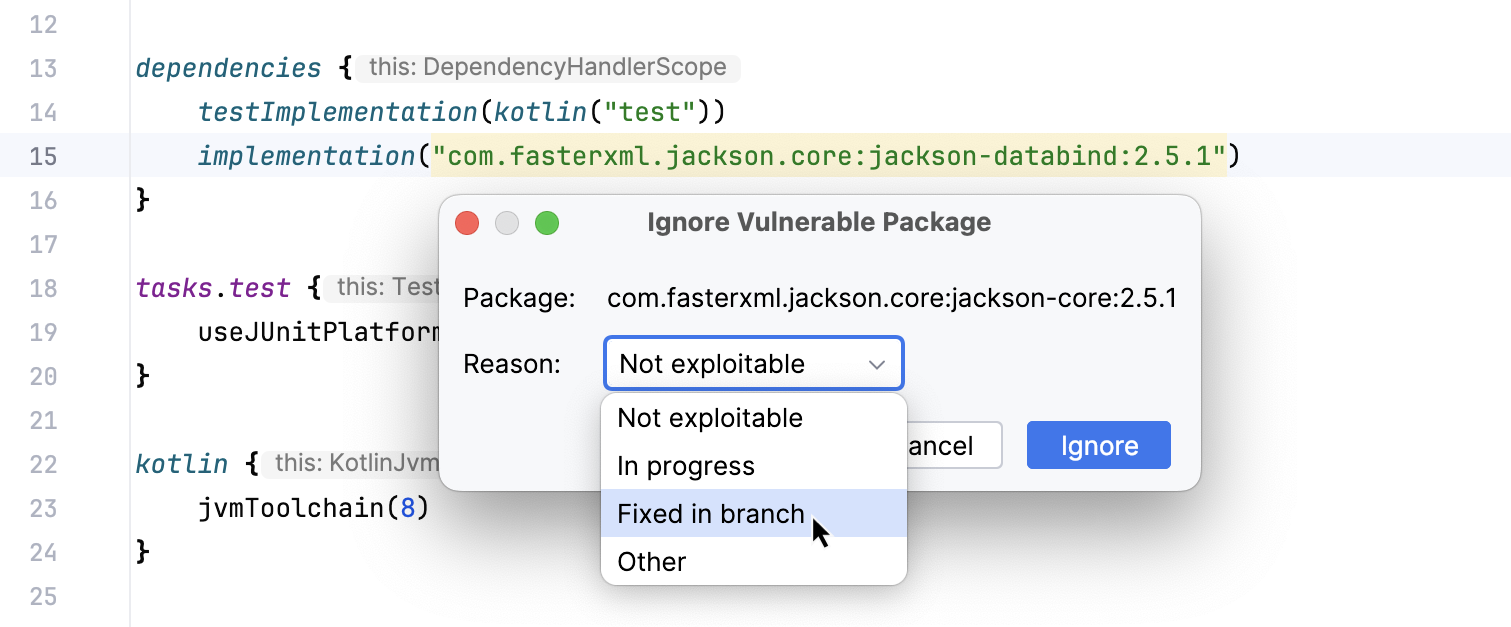
Open pom.xml or build.gradle in the editor, place the caret at a highlighted package, and press Alt+Enter.
From the list of suggestions, select Ignore vulnerable <package name and version>, and in the dialog that opens, select a reason for ignoring the dependency. Click Ignore.
To access the list with ignored vulnerabilities, press Ctrl+Alt+S to open the IDE settings and then select . Expand the Security node and click Vulnerable declared dependency. The list is located in the Options section in inspection details.
Learn how to share inspection profiles from Synchronize profiles between computers.
Find vulnerable APIs
The Vulnerable API usage inspection automatically highlights vulnerable APIs and open-source libraries right in your code. You can also run the inspection manually to get a report about all vulnerable APIs and open-source libraries in your project.
Show vulnerable APIs in the editor
Hover over the detected problem in the editor.
A popup with vulnerability details appears.
Place the caret at the problem, press, and select Go to file with declared dependency.
You will be taken to the file in which the dependency is defined.
Place the caret at a highlighted package and press Alt+Enter to see the suggested fixes. They may suggest updating to a safe version, visiting the Mend.io website to learn more about a particular vulnerability, or ignoring the vulnerability.
Analyze code to find all vulnerable APIs
Press Ctrl+Alt+Shift+I or go to in the main menu.
Type
Vulnerable API usageand double-click the inspection to open the dialog with settings.Select the scope of files that you want to analyze.
The File mask(s) option helps you narrow down the number of files that will be inspected. Specify a pattern of characters and wildcards that matches the names of files you want to analyze. Use a comma to separate multiple file masks.
Click OK to run the inspection.
The result appears in the Problems tool window ( or Alt+6) from which you can navigate to the file with declared vulnerable dependencies, suppress the inspection, or generate a report.
Report false positives
If you believe that a dependency identified as vulnerable is safe, you can report a false positive.
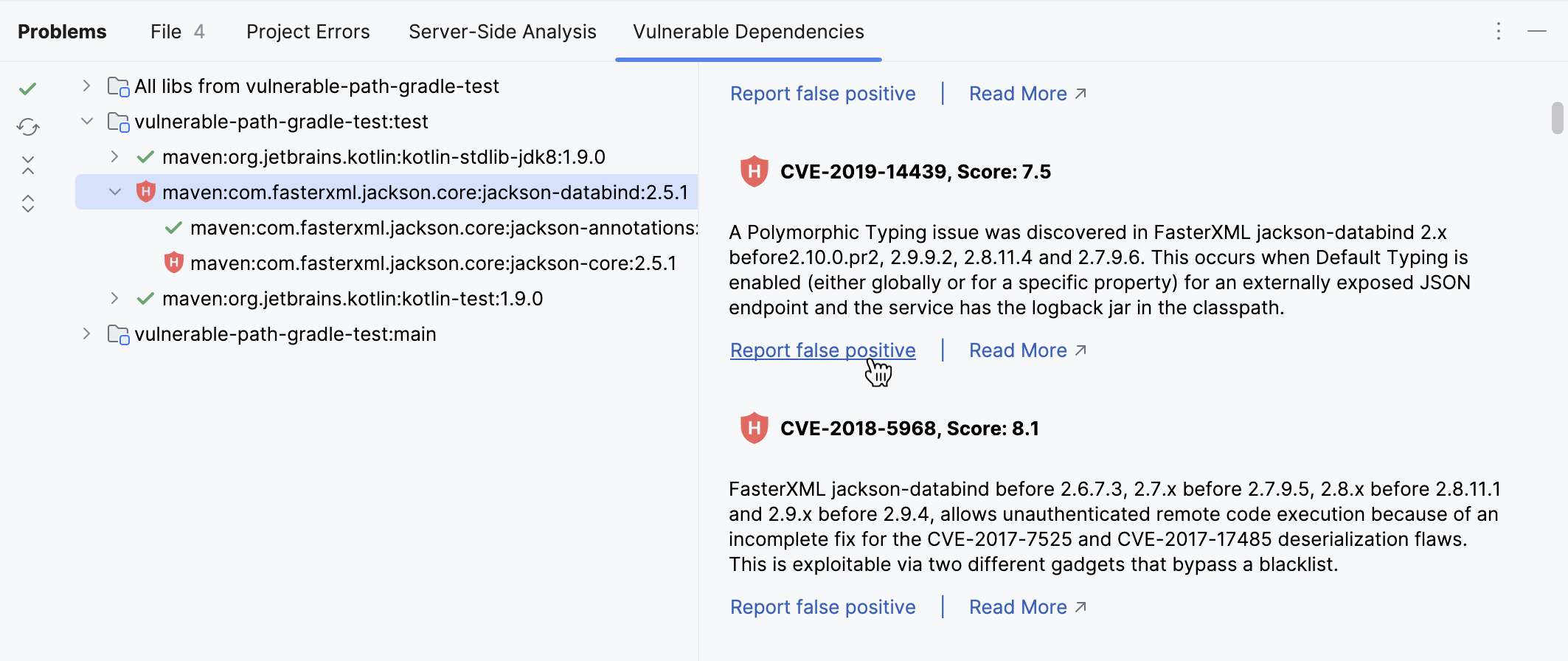
Click a dependency on the Vulnerable Dependencies tab of the Problems tool window ( or Alt+6) to open its description.
Locate the vulnerability that you want to report and click Report false positive.
You will see a notification with confirmation.
Malicious dependencies
The Package Checker plugin features the Malicious dependency inspection that detects malicious NPM and PyPI dependencies declared in your project. Fixing the reported problems stops your software from being compromised by an attacker.
Show malicious dependencies
Open a file in which NPM or PyPI dependencies are declared.
The IDE highlights the dependencies that are considered malicious.
It is recommended that you remove the detected dependencies. Malicious dependencies data is provided by Mend.io.
Find malicious dependencies on commit
Press Alt+0 to open the Commit tool window and click Show Commit Options
.
Enable the Check malicious dependencies option.
Configure Security inspections
You can change the severity of the Security inspections, enable and disable them, and configure problem highlighting in settings.
Press Ctrl+Alt+S to open settings and then select .
From the options on the right, select the Security node and select the name of the inspection.
Change the severity, scope, and highlighting as needed. Click OK to save the changes.