User Authentication
Space comes with a built-in authentication module that lets users log in with Space username and password. To let users log in to Space with their third-party accounts, such as Google or GitHub, you can enable LDAP and third-party account authentication by configuring and enabling additional Auth modules.
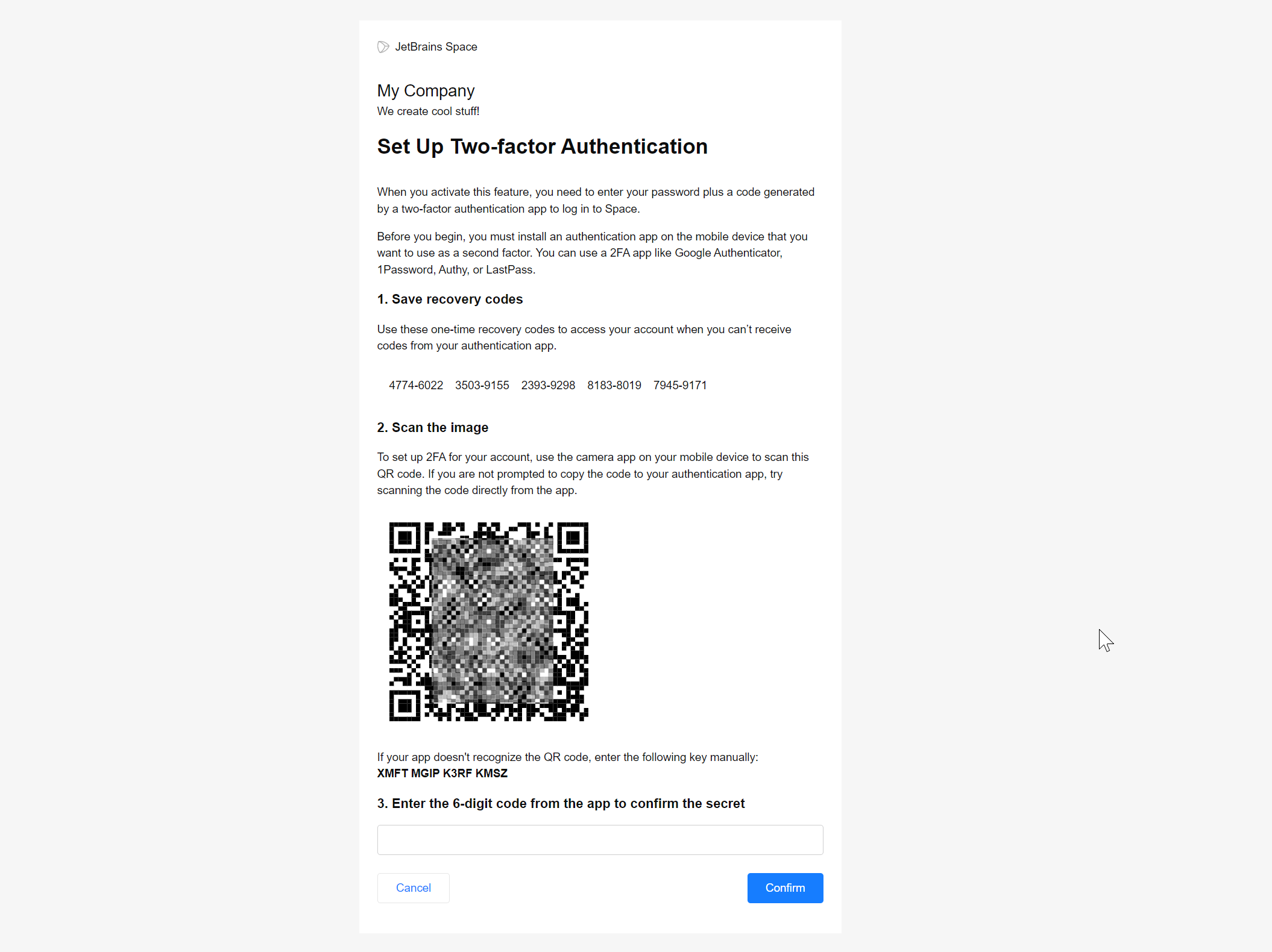
For additional security, each Space user can individually set up and enable 2FA (two-factor authentication) which will work with the built-in authentication. As a system administrator you can enforce 2FA requirement making it mandatory.
Built-in authentication module
The Built-in Auth Module is the native authorization scheme for managing user account credentials. It is enabled by default.
Third-party authentication modules
These authentication modules allow the users to log in with third-party account credentials.
Open LDAP and Active Directory authentication modules
The Open LDAP and Active Directory authentication modules let users log in to Space with credentials that are stored in a directory service.
Logging in with multiple credentials
Depending on the auth modules enabled and their configuration, it may be possible for a user to log in with different credentials, all of which will be tied to a single username.
A list of credentials which the member has ever logged in with is shown in the member profile under Logins.
Detach credentials from a user account
Unwanted credentials can be removed from the user account. For example, if the user has mistakenly logged in with their home Google credentials instead of the work one, the wrong credentials can be detached from their username:
Open the user profile.
On the left-hand sidebar, choose Logins.
Locate the wrong credentials on the list and click Detach.
If built-in module credentials were detached by mistake, access can be restored by resetting password on the login form.
Require users to enable two-factor authentication
You can enforce two-factor authentication policy by requiring users with certain roles to set up 2FA for their accounts. With the 2FA requirement enabled, users won't be able to log in to Space until they provide a security code generated by a two-factor authentication app that users need to install and set up.
To turn on 2FA authentication requirement:
On the main menu, click
 Administration and choose Roles.
Administration and choose Roles.On the left pane, choose the role you want to set the 2FA requirement for and turn on the toggle Require two-factor authentication:

You can enable the requirement for the following roles:
System Admin
Member
Any custom role
Note that setting the requirement for the Member and System Admin roles will make the 2FA mandatory for all users.
After the requirement is on, affected users that don't have 2FA enabled for their accounts will be asked to set it up when they try to log in to Space: