Datalore On-Premises in AWS
This section provides AWS-related information recommended for consideration when planning Datalore On-Premises deployment in AWS.
note
For successful installation and subsequent maintenance of Datalore On-Premises, good knowledge of cloud computing and AWS is strongly advised. Otherwise, we recommend considering our professional support services or managed cloud installation option.
Datalore has been tested and can be run in all the AWS regions where Elastic Kubernetes is available (excluding AWS China, which is currently not supported).
note
While we do not expect any significant issues with Datalore in the AWS China region, it has not been tested yet. Therefore, we cannot provide a proper level of support yet. AWS China is likely to come soon, once tested and verified.
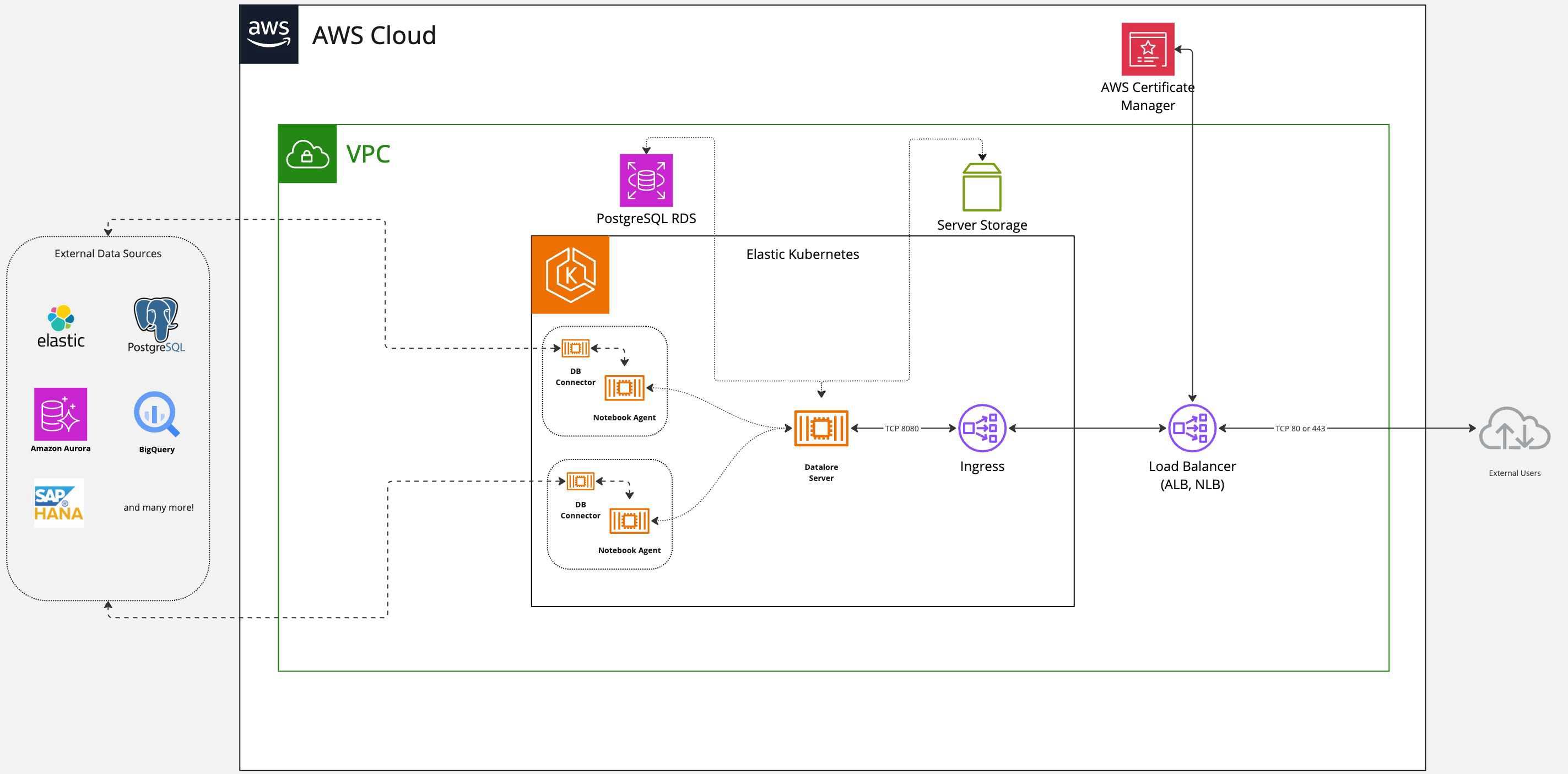
The below diagram represents the most typical Datalore deployment within the AWS environment (click for full screen view).
note
The full list of the supported data sources is available in the Connect to data chapter.
The above diagram shows an approximate approach to Datalore deployment, leaving out some environmental-specific components (for example, the networking part).
Below are some of the key aspects for environment administrators to consider when planning their Datalore deployment tailored to their needs.
Make sure the IAM entity used to deploy Datalore has sufficient permissions to interact with the EKS cluster. This will enable you to provision new entities (StatefulSet, Pod, Ingress, ConfigMap, Secret) in a desired namespace.
For more guidance, refer to the EKS documentation about the managing access entries.
By its nature Datalore has also to communicate with various data sources, which could be located anywhere: from the same AWS region to an on-premises database exposed via a VPN.
Therefore, it is required to configure an appropriate egress security group's rules to allow Datalore agents to communicate with these data sources. The same rule applies both for when the data source is remote (on-premises) or local to the environment (Datalore and the database deployed in different VPCs which are connected via VPC peering, as an example).
note
For example, if the datasource is a PostgreSQL database, make sure outgoing connections for the TCP port 5432 are allowed.
For its own operation, Datalore requires a PostgreSQL database. We recommend referring to Getting started with RDS for database provisioning instructions.
tip
Although Amazon Aurora can also be used together with Datalore, its testing is still in progress, and we, therefore, do not yet recommend using Aurora with Datalore.
Thanks for your feedback!
